
A relatively new malware service called FormBook is seeing a rise in adoption and could become a significant source of malicious email attachments targeting Windows users.
FireEye researchers today posted an analysis of FormBook malware after detecting a surge in activity beginning in July targeting businesses in the US and South Korea.
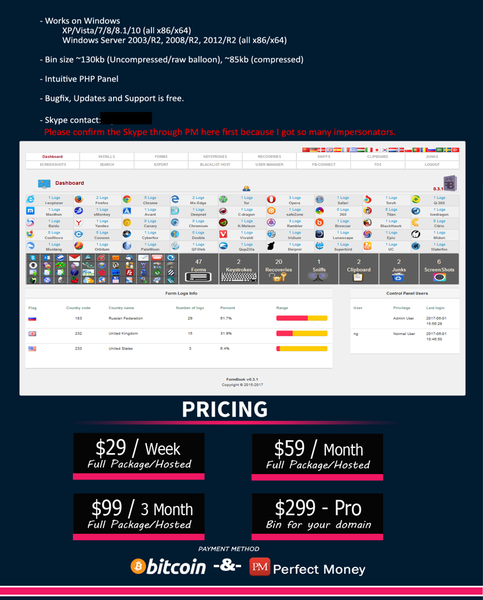
FormBook is another example of malware-as-a-service and is advertised on cybercrime forums from $59 per-month or $299 for the “Pro” edition. The seller touts an “extensive and powerful internet monitoring experience” that works “perfectly on all versions of Windows”.
The malware isn’t quite as dangerous as malware for banking stealing credentials, but can log keystrokes, nab content copied to the clipboard, and grab data from HTTP forms. It can also steal passwords from browsers and email clients, and take screenshots.
Other countries being targeted include India, Germany, Belgium, Australia, Japan, Sweden, Saudi Arabia, and France. About 40 percent of FormBook malware recipients are in manufacturing.
Yesterday the Internet Storm Centre detailed an email containing a fake FedEx Office delivery notice and a link to a supposed receipt that leads to a non-FedEx site that downloads an a RAR archive with malware. FireEye's analysis suggests this is just one of several groups who've adopted FormBook and are spreading it through email.
The seller of the malware service doesn’t offer a tool for customers to build the malware on their own, but offers to generate the executables for paying customers who also get access to the panel for managing and monitoring infections.
ArborNetworks last month posted its analysis of the malware noting that it was “seeing more and more” of FormBook. The cheap price, availability on popular hacker forums, and an apparent cracked version of the malware builder is helping it spread through multiple campaigns, according to ArborNetworks.
Other features of FormBook include remote commands from it can receive from the command and control server:
- Update bot on host system
- Download and execute file
- Remove bot from host system
- Launch a command via ShellExecute
- Clear browser cookies
- Reboot system
- Shutdown system
- Collect passwords and create a screenshot
- Download and unpack ZIP archive
According to FireEye, attack groups using FormBook are delivering the malware through PDFs with download links, Word and Excel files with malicious macros, and archive files, including ZIP, RAR, ACE, and ISOs, which contain executable payloads. The PDF campaigns are using bogus FedEx and DHL delivery themed messages.
At 71 percent the US makes up the vast majority of targets of the PDF campaign, and the second most targeted nation at nine percent is Australia.
The macro-laced Word and Excel files attempt to dupe victims with bogus subject lines about new orders, RFQs, and urgent purchase orders.
The archive campaign meanwhile leans on subjects like payment confirmations from banks, remittance confirmation, new orders, and request for quotes.
Both ArborNetworks and FireEye note the malware doesn’t standout from other malware in functionality and distribution methods, but note the low cost and open availability make it attractive.