 Credit: Michael Simon/IDG
Credit: Michael Simon/IDG
If you aren’t already protecting your most personal accounts with two-factor or two-step authentication, you should be. An extra line of defense that’s tougher than the strongest password, 2FA is extremely important to blocking hacks and attacks on your personal data. If you don’t quite understand what it is, we’ve broken it all down for you.
Two-factor-authentication: What it is
Two-factor authentication is basically a combination of two of the following factors:
- Something you know
- Something you have
- Something you are
Something you know is your password, so 2FA always starts there. Rather than let you into your account once your password is entered, however, two-factor authentication requires a second set of credentials, like when the DMV wants your license and a utility bill. So that’s where factors 2 and 3 come into play. Something you have is your phone or another device, while something you are is your face, irises, or fingerprint. If you can't provide authentication beyond the password alone, you won't be allowed into the service you're trying to log into.
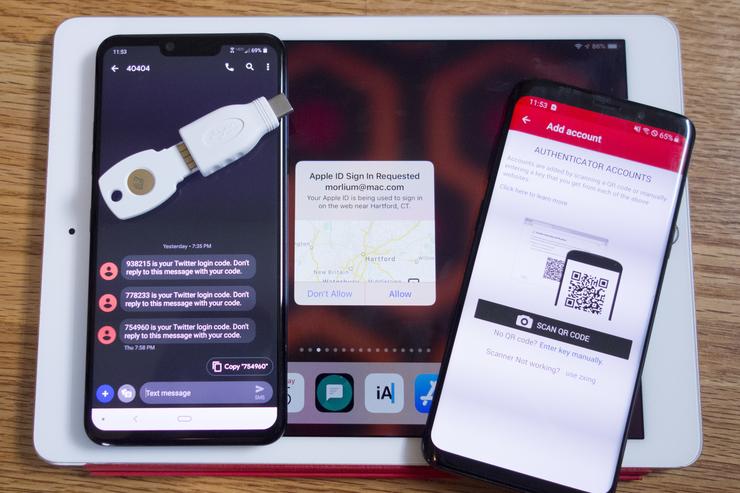
So there are several options for the second factor: SMS, authenticator apps, Bluetooth-, USB-, and NFC-based security keys, and biometrics. So let’s take a look at your options so you can decide which is best for you.
Two-factor-authentication: SMS
 Michael Simon/IDG
Michael Simon/IDG
When you choose SMS-based 2FA, all you need is a mobile phone number.
What it is: The most common “something you have” second authentication method is SMS. A service will send a text to your phone with a numerical code, which then needs to be typed into the field provided. If the codes match, your identification is verified and access is granted.
How to set it up: Nearly every two-factor authentication system uses SMS by default, so there isn’t much to do beyond flipping the toggle or switch to turn on 2FA on the chosen account. Depending on the app or service, you’ll find it somewhere in settings, under Security if the tab exists. Once activated you’ll need to enter your password and a mobile phone number.
How it works: When you turn on SMS-based authentication, you’ll receive a code via text that you’ll need to enter after you type your password. That protects you against someone randomly logging into your account from somewhere else, since your password alone in useless without the code. While some apps and services solely rely on SMS-based 2FA, many of them offer numerous options, even if SMS is selected by default.
 IDG
IDG
With SMS-based authentication, you’ll get a code via text that will allow access to your account.
How secure it is: By definition, SMS authentication is the least secure method of two-factor authentication. Your phone can be cloned or just plain stolen, SMS messages can be intercepted, and by nature most default messaging apps aren’t encrypted. So the code that’s sent to you could possibly fall into someone’s hands other than yours. It's unlikely to be an issue unless you're a valuable target, however.
How convenient it is: Very. You’re likely to always have your phone within reach, so the second authentication is super convenient, especially if the account you’re signing into is on your phone.
Should you use it? Any two-factor authentication is better than none, but if you’re serious about security, SMS won’t cut it.
Two-factor-authentication: Authenticator apps
 Authenticator apps
Authenticator apps
Authenticator apps generate random codes that aren’t delivered over SMS.
What it is: Like SMS-based two-factor authentication, authenticator apps generate codes that need to be inputted when prompted. However, rather than sending them over unencrypted SMS, they’re generated within an app, and you don’t even need an Internet connection to get one.
How to set it up: To get started with an authentication app, you’ll need to download one from the Play Store or the App Store. Google Authenticator works great for your Google account and anything you use it to log into, but there are other great one’s as well, including Authy, LastPass, Microsoft and a slew of other individual companies, such as Blizzard, Sophos, and Salesforce. If an app or service supports authenticator apps, it’ll supply a QR code that you can scan or enter on your phone.
How it works: When you open your chosen authenticator app and scan the code, a 6-figure code will appear, just like with SMS 2FA. Input that code into the app and you’re good to go. After the initial setup, you’ll be able to go into the app to get a code without scanning a QR code whenever you need one.
 IDG
IDG
Authenticator apps generate randome codes every 30 seconds and can be used offline.
How secure it is: Unless someone has access to your phone or whatever device is running your authenticator app, it’s completely secure. Since codes are randomized within the app and aren’t delivered over SMS, there’s no way for prying eyes to steal them. For extra security, Authy allows you to set pin and password protection, too, something Google doesn’t offer on its authenticator app.
How convenient it is: While opening an app is slightly less convenient than receiving a text message, authenticator apps don’t take more than few seconds to use. They’re far more secure than SMS, and you can use them offline if you ever run into an issue where you need a code but have no connection.
Should you use it? An authenticator app strikes the sweet spot between security and convenience. While you might find some services that don’t support authenticator apps, the vast majority do.
Two-factor authentication: Universal second factor (security key)
 Michael Simon/IDG
Michael Simon/IDG
As their name implies, Security keys are the most secure way to lock down your account.
What it is: Unlike SMS- and authenticator-based 2FA, universal second factor is truly a “something you have” method of protecting your accounts. Instead of a digital code, the second factor is a hardware-based security key. You’ll need to order a physical key to use it, which will connect to your phone or PC via USB, NFC, or Bluetooth.
You can buy a Titan Security Key bundle from Google for $50, which includes a USB-A security key and a Bluetooth security key along with a USB-A-to-USB-C adapter, or buy one from Yubico. An NFC-enabled key is recommended if you’re going to be using it with a phone.
How to set it up: Setting up a security key is basically the same as the other methods, except you’ll need a computer. You’ll need to turn on two-factor authentication, and then select the “security key” option, if it’s available. Most popular accounts, such as Twitter, Facebook, and Google all support security keys, so your most vulnerable accounts should be all set. However, while Chrome, Safari, and Microsoft’s Edge browser all support security keys, Apple’s Safari browser does not, so you’ll be prompted to switch during setup.
Once you reach the security settings page for the service you're enabling 2FA with, select security key, and follow the prompts. You’ll be asked to insert your key (so make sure you have an USB-C adapter on hand if you have a MacBook) and press the button on it. That will initiate the connection with your computer, pair your key, and in a few seconds your account will be ready to go.
How it works: When an account requests 2FA verification, you’ll need to plug your security key into your phone or PC’s USB-C port or (if supported) tap it to the back of your NFC-enabled phone. Then it’s only a matter of pressing the button on the key to establish the connection and you’re in.
 IDG
IDG
Setting up your security key with your Google account is a multi-step process.
How secure it is: Extremely. Since all of the login authentication is stored on a physical key that is either on your person or stored somewhere safe, the odds of someone accessing your account are extremely low. To do so, they would need to steal your password and the key to access your account, which is very unlikely.
How convenient it is: Not very. When you log into one of your accounts on a new device, you’ll need to type your password and then authenticate it via the hardware key, either by inserting it into your PC’s USB port or pressing it against the back of an NFC-enabled phone. Neither method takes more than a few seconds, though, provided you have your security key within reach.
Two-factor authentication: Google Advanced Protection Program
What it is: If you want to completely lock down your most important data, Google offers the Advanced Protection Program for your Google account, which disables everything except security key-based 2FA. It also limits access your emails and Drive files to Google apps and select third-party apps, and shuts down web access to browsers other than Chrome and Firefox.
How to set it up: You’ll need to make a serious commitment. To enroll in Google Advanced Protection, you’ll need to purchase two Security Keys: one as your main key and one as your backup key. Google sells its own Titan Security Key bundle, but you can also buy a set from Yubico or Feitian.
Once you get your keys, you’ll need to register them with your Google account and then agree to turn off all other forms of authentication. But here’s the rub: To ensure that every one of your devices is properly protected, Google will log you out of every account on every device you own so you can log in again using Advanced Protection.
How it works: Advanced Protection works just like a security except you won’t be able to choose a different method if you forgot or lost your security key.
How secure it is: Google Advanced Protection is basically impenetrable. By relying solely on security keys, it makes sure that no one will be able to access your account without both your password and physical key, which is extremely unlikely.
How convenient it is: By nature, Google Advanced Protection is supposed to make it difficult for hackers to access your Google account and anything associated with it, so naturally it’s not so easy for the user either. Since there’s no fallback authentication method, you’ll need to remember your key whenever you leave the house. And when you run into a roadback—like the Safari browser on a Mac—you’re pretty much out of luck. But if you want your account to have the best possible protection, accept no substitute.
Two-factor authentication: Biometrics
 Christopher Hebert/IDG
Christopher Hebert/IDG
Nearly every smartphone made today has some form of secure biometrics built into it.
What it is: A password-free world where all apps and services are authenticated by a fingerprint or facial scan.
How to set it up: You can see biometrics at work when you opt to use the fingerprint scanner on your phone or Face ID on the iPhone XS, but at the moment, biometric security is little more than a replacement for your password after you login in and verify via another 2FA method.
How it works: Like the way you use your fingerprint or face to unlock your smartphone, biometric 2FA uses your body's unique characteristics as your password. So your Google account would know it was you based on your scan when you set up your account, and it would automatically allow access when it recognized you.
How secure it is: Since it’s extremely difficult to clone your fingerprint or face, biometric authentication is the closest thing to a digital vault.
How convenient it is: You can’t go anywhere without your fingerprint or your face, so it doesn’t get more convenient than that.
Two-factor authentication: iCloud
 Michael Simon/IDG
Michael Simon/IDG
Apple sends a code to one of your trusted devices when it needs authentication to access an account.
What it is: Apple has its own method of two-factor authentication or your iCloud and iTunes accounts that involves setting up trusted Apple devices (iPhone, iPad, or Mac—Apple Watch isn't supported) that can receive verification codes. You can also set up trusted numbers to receive SMS codes or get verification codes via an authenticator app built into the Settings app.
How to set it up: As long as you’re logged into into your iCloud account, you can turn on two-factor authentication from pretty much anywhere. Just go into Settings on your iOS device or System Preferences on your Mac, PC, or Android phone, then Security, and Turn On Two-Factor Authentication. From there, you can follow the prompts to set up your trusted phone number and devices.
How it works: When you need to access an account protected by 2FA, Apple will send a code to one of your trusted devices. If you don’t have a second Apple device, Apple will send you a code via SMS or you can get one from the Settings app on your iPhone or System preferences on your Mac.
 IDG
IDG
When Apple needs a code to log into an account, it sends it to one of your trusted devices.
How secure it is: It depends on how many Apple devices you own. If you own more than one Apple device, it’s very secure. Apple will send a code to one of your other devices whenever you or someone else tries to log into your account or one of Apple’s services on a new device. It even tells you the location of the request, so if you don’t recognize it you can instantly reject it, before the code even appears.
If you only have one device, you’ll have to use SMS or Apple’s built-in authenticator, neither of which is all that secure, especially since it’s likely to both be done using the same device. Also, Apple has a weird snafu that sends the 2FA access code to the same device when you manage your account using a browser, which also defeats the purpose of 2FA.
How convenient it is: If you’re using an iPhone and have an iPad or Mac nearby, the process takes seconds, but if you don’t have an Apple device within reach or are away from your keyboard, it can be tedious.