Phishers target middle management
- 24 June, 2015 01:25
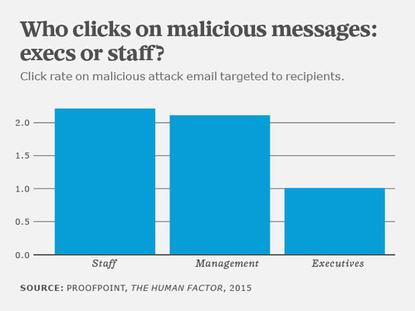
The study found that managers doubled their click rates on malicious emails in 2014 compared to the previous year -- a marked change from 2013 for managers, who were much less frequently targeted by malicious emails in the past.
Phishing scammers have infiltrated the enterprise and they're finding easy prey, but it's not in the C-suite as previously thought. Attackers are exploiting the multitasking, often overloaded middle management ranks, according to research by security and compliance firm Proofpoint.
"2014 was clearly the year that attackers went corporate, and they targeted middle management because it's profitable," says Kevin Epstein, vice president, advanced security and governance. The study examined more than a million workers' email and social media activities at work over a one-year period.
The study found that managers doubled their click rates on malicious emails in 2014 compared to the previous year -- a marked change from 2013 for managers, who were much less frequently targeted by malicious emails in the past.
What makes middle managers an easy target? "Our suspicion is they're under pressure to move through emails faster or the email itself is more compelling" than in previous scams, Epstein says.
Middle managers are also clicking on emails more quickly. In 2013, 40% of middle managers would click on the first day that a malicious email appeared and 25% took a week. In 2014, two out of three end users clicked on the first day, according to the study. What's more, managers and staff clicked on links in malicious messages two times more frequently than executives.
When employees click on a malicious email within the first 24 hours, "as a defender you don't have much time," he says. "If the email makes it through that gateway, bad guys start pulling data out of your company within hours of it being installed."
Proofpoint used data gathered from its own technology that includes exact user information about which users clicked on bad links. Billions of incoming and outgoing emails and social media content were collected from a subset of its corporate customers. While Proofpoint doesn't usually have access to this data, the customer group provided the job titles of the bad clickers for the study. Using that data, "we're able to see trends in what sort of functions and levels are being targeted," Epstein says.
Cybercriminals are indeed targeting the enterprise, says Stu Sjouwerman, CEO of security awareness training company KnowBe4. "I can certainly see why [middle managers] would have a click load increase. The average person gets 40 emails a day. Middle management gets 100 to 200 [emails] a day. That would get double or triple click-through rates compared to the average worker in an office," he says.
Some of the bad guys' tactics include choosing a time of day when email traffic is busiest, which increases the likelihood of a mindless click onto a malicious email. Tuesday mornings are a favorite for scammers with 17% more clicks that day, according to the Proofpoint study. Managers are also falling for simple tactics, such as bogus voicemail attachments marked urgent or fax attachments. Sjouwerman says email spoofs appearing to come from the company's IT department requiring a change of password or updated email information are also popular workplace phishing scams.
Though it appears that middle managers are in the crosshairs, Sjouwerman wonders if they are simply victims rather than targets.
"The bad guys don't really care who they send the phishing attacks to they just find a bunch of email addresses for a particular organization and they send it to everyone," Sjouwerman says. "The first person who clicks gets the bonus of being infected with a Trojan that tunnels into the network. It's more likely that middle managers are under the highest pressure. They start clicking on everything quickly and don't take those two seconds to think is this a scam or not?"
Persistence also pays off for scammers. Malicious emails are rarely sent in isolation--with some arriving faster than others. A campaign of just 10 emails yields a greater than 90% chance that at least one person will become the criminal's prey, according to Verizon's 2015 Data Breach Investigations Report. Middle managers may click on links and attachments just to make the emails stop, industry-watchers say.
[ ALSO: Deconstructing an IRS Phishing scam ]
Inside an organization, attackers are evenly targeting all departments, but finance, sales and procurement staff clicked on malicious links 50-80% more on average than other departments, according to the Proofpoint study. These groups have access to payments and funds transfers an appealing target for phishing scammers.
In Verizon's data breach report, workers in communications, legal and customer services were the most likely culprits to open a phishing email, but the report did not identify the bad clickers by their titles.
Verizon also illustrated how quickly an attacker can get a foot in the door. It examined over 150,000 e-mails sent as part of sanctioned tests by two of its security awareness partners and measured how much time had passed from when the message was sent to when the recipient opened it, and if they were influenced to click or provide data, which is where the real damage is done. The data showed that nearly 50% of users open e-mails and click on phishing links within the first hour.
Regardless of whether middle managers are targets or victims, companies must protect them and all employees from the risks, security experts say.
Sjouwerman calls for a six-layer plan, starting with awareness education that includes simulated phishing attacks to continually remind employees of the risks. Security must also be addressed at the firewall, network, computer, application and data layers, he adds.
"Antivirus these days gives you a false sense of security and it's not able to block a lot of these ransomware attacks because they're sitting inside a zip file within a zip file," for instance, Sjouwerman says. "It's the human that's being social engineered" to open these files, and so awareness programs are critical, he adds.
He also recommends whitelisting, which is creating a simple list of applications that have been granted permission by the user or an administrator. When an application tries to execute, it is automatically checked against the list and, if found, allowed to run. "It's a safer way to protect end points from getting infected," Sjouwerman says.
Verizon calls for a three-point approach to protecting employees from phishing scams, including better e-mail filtering before messages arrive in user in-boxes, a security awareness program, and improved detection and response capabilities.
Proofpoint executives say information security policy and practices must pay special attention to non-executive employees, where most of the compromises will originate. Security teams should also develop granular policies and defenses for departments that are particularly vulnerable.

