Enterprises should use RFPs to force industry to improve security
- 05 March, 2019 13:08
Organisations are leaving themselves exposed by failing to demand adequate security protections when buying new technology, according to a senior Cisco executive who warned that security and networking specialists must work together better to close persistent gaps.
Cybercriminals had evolved from simply trying to steal data, to a position where they are infiltrating networks and targeting business availability, Scott Harrell, senior vice president and general manager of Cisco’s Enterprise Networking business, told attendees at the Cybersecurity Innovation Day at Cisco Live! in Melbourne.
Some attackers are burying cryptomining agents deep within enterprise networks and quietly hogging resources for their own purposes, while other attackers are compromising network routers and switches to monitor daily activities and facilitate other attacks.
“If you get hold of a router or switch, it survives reboot and it’s invisible,” Harrell said. “Attackers can understand everything that’s going on in an organisation. You may already be exploited by this – and the question is, are you ready to defend against it, and will you be ready when it happens?”
A lack of co-ordination between security and networking teams had frequently perpetuated the weaknesses facilitating these breaches, with security teams arguing that router and switch configurations were the responsibility of networking teams.
Lingering attitudes like this had left networking equipment exposed for long periods, with many companies often finding they are running old versions of networking operating systems with known vulnerabilities that have never been patched.
That left many core network devices as exposed as commonly-maligned Internet of Things (IoT) devices, whose simplistic designs have become synonymous with insecurity due to their inability to be updated en masse.
The proliferation of insecure endpoints “brings new challenges,” Harrell said. “It’s not just that the OS posture of these devices is insanely poor, but that you can’t put an agent on them. You’ve lost a key piece of the kill chain, yet you have so many of these devices that you have to add a zero on the end every year to keep track of how many you have.”
Rethinking secure network architectures
With endpoint security being overrun, the common need to tighten network security would provide an opportunity for security and networking specialists to put aside their historical differences and work together to rearchitect enterprise networks for security.
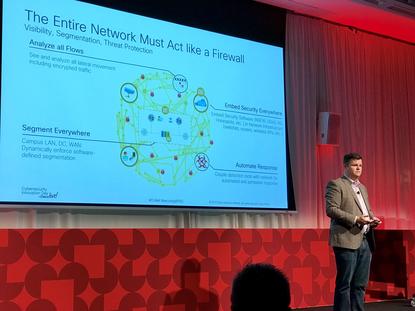
A key part of this effort, Harrell said, is “to embed threat protection and visibility into every node of the network. You have lost parts of the kill chain, and have lost the ability to watch every endpoint – so you need to think differently. The entire network must start to act like a firewall.”
Cisco had been addressing the problem by improving analysis of data flows, embedding security everywhere on the network, heavily segmenting the network, and facilitating an automated response to security issues that leverages the flexibility of security controls including software-defined WAN security, centralised cloud security, and colocation security.
“Your network is a target for these availability-based attacks,” Harrell said. “You can dramatically reduce the scope of an incident by simply segmenting your network – but it’s hard to do.”
Organisations are making it even harder for themselves with procurement processes that continue ignoring the importance of better security, he said.
Requests for proposal (RFPs) needed to demand suppliers provide security capabilities including the ability to securely boot from signed images; a Trust Anchor module (TAm) to manage network trust; and runtime defences that can detect malware trying to insert itself into networked devices.
Business customers could make these capabilities more common by forcing suppliers to provide them – but “I see a lot of enterprise RFPs and they are in almost none of them,” Harrell said. That would only change with smarter procurement of appropriate technology: “If you start forcing this with RFPs, I guarantee that this will be across every bid,” he said.
“It’s a non-trivial engineering exercise to build this and keep it up to date,” he added, noting that even Cisco had to work to retrofit many of these capabilities to the technology it acquired from purchased companies.
“Where your organisation puts in a device that does not have these kinds of controls, you are putting in a hardware-level vulnerability and you should expect that it will be breached. As soon as you build it, the attackers start thinking about how to exploit it – so enterprises need to help push the industry this way. Security ought to be in every single RFP.”

